CTF Server
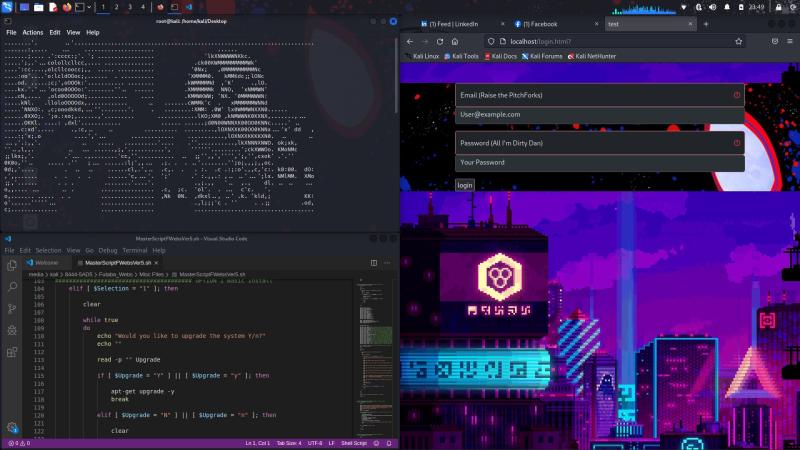
This is a custom portable CTF server that I made! Try it out!
RoyMBull Github
Take a loot at some of my projects available on my GitHub page!
Exploit Videos

Check out some of my live hacking exploit demonstrations.





